Enterprise payment security starts with choosing the right payment architecture. In 2024, 90% of U.S. companies experienced cyber fraud, yet most organizations overlook one of the most critical security decisions: selecting between push and pull payment systems. This architectural choice directly impacts fraud prevention, operational risk, and regulatory compliance.
The stakes couldn't be higher. Nearly 60% of companies said the financial impact of payment fraud they experienced in 2024 was over $5M compared to just a quarter who said this the year prior, which is a 136% increase. As payment fraud evolves at breakneck speed, the underlying architecture of how money moves becomes a critical line of defense.
Understanding Payment Architecture Fundamentals
Before diving into security implications, let's establish what distinguishes push from pull payment systems at their core.
Push Payments: Payer-Initiated Control
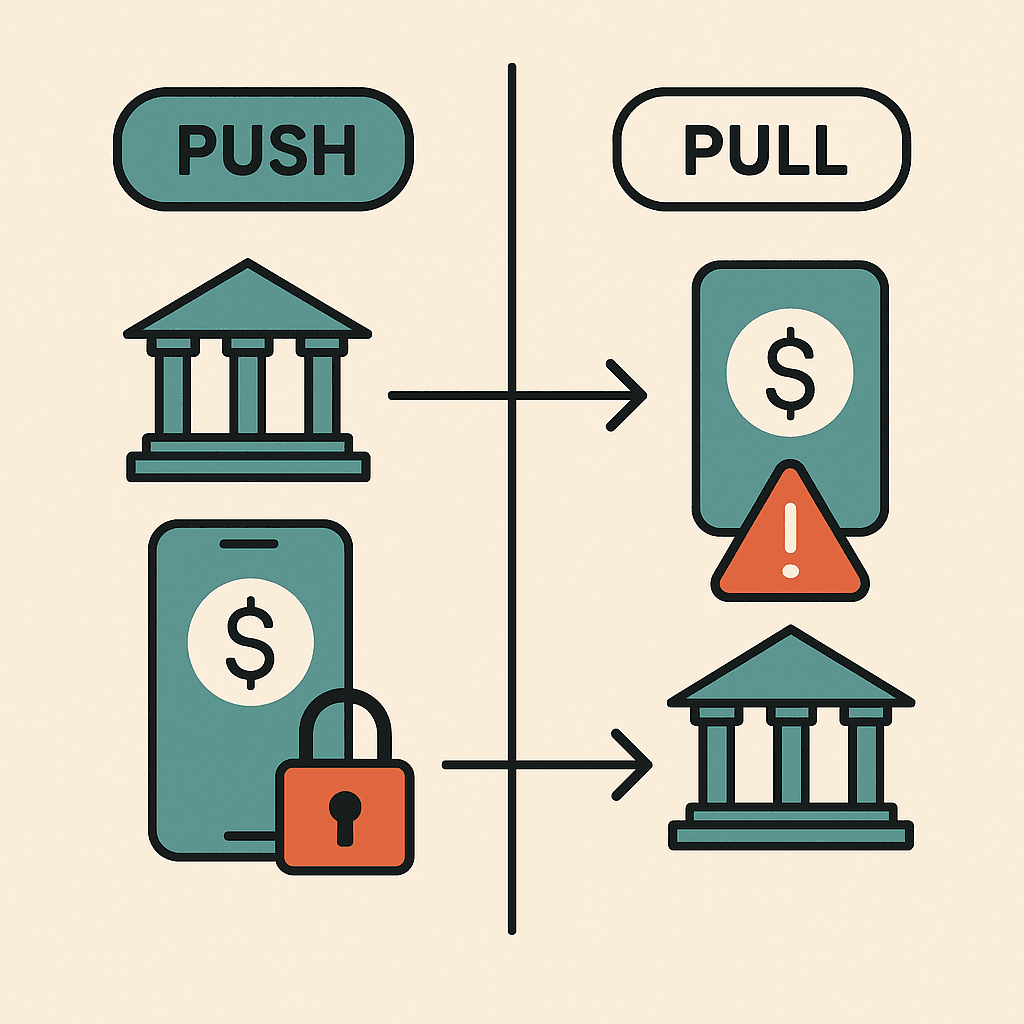
Push payments allow only the payer to originate a transaction. In this model, the sender initiates and authorizes the transfer of funds to a recipient. Think of wire transfers, real-time payment systems like FedNow and RTP, or even cryptocurrency transactions where only the holder of private keys can spend those funds.
Key characteristics of push systems:
Origination Control: Only the payer can start the transaction
Active Authorization: Requires explicit action from the fund holder
Real-time Processing: Push payments give payers control over who and how they send money, and payments are handled according to the strict financial policies of the participating banks
Cancellation Window: Often allows cancellation before processing
Pull Payments: Payee-Initiated Convenience
A pull payment system allows payees to pull funds out of a payer's account into their own. In a pull system, the payee is the originator of the transaction. This includes traditional direct debits, subscription billing, and ACH transfers where merchants withdraw funds from customer accounts using stored payment credentials.
Pull payment characteristics:
Recipient Control: The payee initiates and controls timing
Pre-authorization Required: Customers must grant permission in advance
Automated Processing: Ideal for recurring transactions
Trust-Dependent: A pull system requires more trust between payers and payees because the payee has more ability to abuse their power
The Security Paradigm: Control vs. Convenience
The fundamental security difference between these architectures lies in who controls transaction initiation—and that control point becomes the primary attack vector.
Push Payment Security Advantages
Reduced Attack Surface With push payments, the security perimeter is clearly defined: only the account holder can authorize outbound transactions. Unlike more manual payment options like checks or money orders, push payments go through encryption and authentication processes that are less likely to be affected by fraud attempts.
Real-time Fraud Prevention Transactions on the blockchain network are approved by thousands of computers and devices. This removes almost all people from the verification process, resulting in less human error and an accurate record of information. Push systems, particularly those built on blockchain infrastructure, benefit from this distributed verification model.
Immediate Cancellation Rights If the payer has any reservations about the payment, they can cancel it before processing. This creates a natural defense against social engineering attacks and provides a recovery window for compromised transactions.
Pull Payment Vulnerabilities
Expanded Attack Vectors Pull systems inherently create more points of potential compromise. Pull systems allow certain entities, such as banks or merchants, to pull money out of payers' accounts and transfer it to their own. Each authorized party becomes a potential attack target.
Information Exposure Requirements A pull system requires payers to provide payees with sensitive financial information, including routing and account numbers, in the case of ACH payments, or a PIN in the case of debit cards. This information sharing multiplies the potential for data breaches.
Delayed Detection Because pull transactions are often automated and recurring, fraudulent activity can continue for extended periods before detection. Unlike push payments where users actively initiate each transaction, pull fraud can compound before victims notice unauthorized withdrawals.
Enterprise-Level Security Implications
For enterprise payments, the choice between push and pull architectures affects not just transaction security, but operational risk management and compliance posture.
Operational Security Benefits of Push Architecture
Reduced Insider Threat Exposure Push systems require active authorization for each outbound payment, creating natural breakpoints that prevent automated fraud. Even if internal systems are compromised, attackers cannot simply redirect recurring payments without triggering additional authentication steps.
Audit Trail Clarity Push payments prioritize encryption and authentication. Robust encryption protocols safeguard the communication channel between the payer's device and the payment service provider, ensuring the confidentiality of sensitive information like payment details. This creates clearer forensic trails for security investigations.
Regulatory Compliance Advantages With increasing regulatory scrutiny on payment security, push architectures align better with compliance frameworks that emphasize user control and transaction transparency. There are various different regulatory frameworks governing push payments across regions and industries, with standards like PSD2 (Payment Services Directive 2) in the UK aiming to enhance security and consumer protection.
When Pull Systems Create Enterprise Risk
Vendor Payment Vulnerabilities Enterprises using pull-based vendor payment systems face concentrated risk. If a payment processor is compromised, attackers can potentially access multiple client accounts through stored authorization tokens.
Subscription Service Exposure Account Takeover (ATO) fraud will likely escalate in 2025 as digital payment platforms and peer-to-peer payment systems grow in popularity. Pull-based subscription services become prime targets because compromised credentials can generate ongoing fraudulent charges.
Cross-Border Complications Pull systems face additional security challenges in international payments where regulatory oversight varies significantly across jurisdictions.
How to Implement Secure Payment Architecture: Best Practices for Banks
Financial institutions implementing crypto mobile payments or stablecoin business accounts need comprehensive security frameworks. Here's how leading banks are approaching payment architecture security:
Step 1: Assess Current Payment Infrastructure Security
Audit existing push vs pull payment vulnerabilities
Evaluate crypto treasury management capabilities
Review DeFi infrastructure readiness for institutional use
Analyze cross-border payment fraud exposure
Step 2: Design Programmable Payment Security Controls
Modern DeFi business banking requires programmable yield while maintaining enterprise-grade security:
Implement smart contract-based authorization controls
Deploy automated fraud detection for crypto cash management
Enable yield generating smart accounts with multi-signature governance
Establish non-custodial yield account procedures
Step 3: Integrate Blockchain Payment Security Features
Deploy Solana DeFi yield protocols with institutional safeguards
Implement pull-based crypto payments with enhanced verification
Enable stablecoin payment processor integration
Establish zero fee payment processor protocols using yield-based revenue
Frequently Asked Questions About Payment Architecture Security
What is the difference between push and pull payment security?
Push payment security gives the payer complete control over transaction initiation, while pull payment security relies on pre-authorized access that creates additional attack vectors for fraudsters.
How do blockchain payments improve enterprise security?
Blockchain payments provide immutable transaction records, eliminate intermediary risks, and enable programmable security controls that traditional payment systems cannot match.
Why are pull-based payments more vulnerable to fraud?
Pull payments require sharing sensitive account information and create ongoing authorization that can be exploited if merchant systems are compromised.
What payment architecture do central banks recommend for CBDCs?
Most central banks are implementing push-based architectures for digital currencies to maintain user control while enabling programmable features.
How can businesses implement crypto payment security best practices?
Start with push-based blockchain payment systems, implement multi-factor authentication, deploy smart contract-based controls, and establish regular security audits.
Blockchain-Enhanced Push Systems
Forward-thinking banks are exploring blockchain-based push payment systems that combine the security benefits of payer-controlled initiation with the efficiency of automated settlement. Many cloud and blockchain-based instant payments systems workflows are built with advanced security measures and AML protections.
Key Implementation Benefits:
Immutable Transaction Records: Blockchain settlements are full and final. Once completed they become an immutable part of the blockchain ledger meaning there are no chargebacks in blockchain payments
24/7 Operation: Blockchains operate 24/7/365 – meaning payments can be sent over weekends, during bank holidays and outside normal banking hours
Reduced Intermediary Risk: Using blockchain cryptography, two parties can complete a transaction without sharing their own information or having to use an intermediary such as a bank
Programmable Yield Integration: Advanced systems enable instant yield DeFi deployment while maintaining push security controls
Smart Pull Systems with Enhanced Controls
For enterprises that require pull functionality, particularly for subscription services or B2B recurring payments—implementing additional security layers becomes critical.
Advanced Authorization Mechanisms: Modern pull systems can incorporate dynamic authorization thresholds, biometric confirmation for large amounts, and real-time spending limits that adapt based on transaction patterns.
Yield-Enabled Security Models: Innovative platforms are now implementing pull payment systems that generate yield on authorized funds until they're actually withdrawn. This approach, pioneered by companies like RebelFi, transforms traditional pull systems by ensuring payers maintain financial benefit from their authorized funds while providing merchants with reliable payment certainty through programmable yield and instant yield DeFi integration.
The Future of Payment Security Architecture
As we look toward 2025 and beyond, the global fraud detection and prevention market size is projected to grow from $63.90 billion in 2025 to $246.16 billion by 2032, exhibiting a CAGR of 21.2%. This explosive growth reflects the urgent need for robust payment security architectures.
Emerging Hybrid Models
Programmable Payment Systems: The next generation of payment architecture combines push security controls with pull convenience through programmable smart contracts. These systems allow for conditional authorization where funds can only be withdrawn when specific criteria are met, creating a middle ground between push and pull models.
AI-Enhanced Security: FIs should invest in advanced AI-based fraud detection tools to counteract evolving threats, focusing on anomaly detection and machine learning algorithms capable of analyzing large volumes of data in real-time. Both push and pull systems benefit from AI integration, but push systems with their clearer authorization patterns provide better training data for machine learning algorithms.
Regulatory Evolution
CBDC Implementation As central banks develop digital currencies, they're primarily implementing push-based architectures that maintain user control while enabling programmable features. Central banks globally are exploring CBDCs to modernize payment systems and enhance financial inclusion.
Enhanced Privacy Requirements Managing customer identities securely is crucial for banks. Blockchain-based identity solutions empower customers to control their data and share it with banks as needed, reducing redundancy and enhancing data protection. Push systems align better with these privacy-first regulatory trends.
Strategic Recommendations for Financial Institutions
Based on current security trends and technological capabilities, here are key recommendations for banks and enterprises:
Prioritize Push Architecture for New Systems
When designing new payment systems, default to push architectures unless pull functionality is absolutely necessary. Push payments often incur lower transaction fees compared to pull payments, particularly where businesses initiate the transactions. Additionally, the reduced risk of fraud associated with push payments can lead to lower overall costs in terms of security measures and fraud prevention.
Implement Programmable Security Controls
For existing pull systems, layer in programmable controls that provide push-like security features:
Dynamic authorization limits
Real-time risk scoring
Automated transaction suspension triggers
Multi-factor authentication for high-value transactions
Consider Blockchain Integration
Major financial institutions, from JPMorgan & Chase Co. (JPM) to Goldman Sachs (GS), have been developing blockchain services, particularly in areas like cross-border payments, know your customer (KYC) verification, and trade finance. Explore blockchain-based payment systems that can provide enhanced security while maintaining operational efficiency.
Develop Hybrid Solutions
Create payment products that offer both architectures depending on use case. High-value, infrequent transactions benefit from push controls, while low-value recurring payments can use enhanced pull systems with appropriate safeguards.
Conclusion: Architecture as Security Strategy
The choice between push and pull payment architectures represents far more than a technical implementation decision, it's a fundamental security strategy that affects fraud risk, regulatory compliance, and operational resilience.
As fraud is evolving faster than ever, financial institutions must recognize that payment architecture choices made today will determine their security posture for years to come. Push architectures, enhanced by blockchain technology and programmable controls, offer the most promising path forward for enterprises seeking to balance security, efficiency, and user experience.
The future belongs to payment systems that combine the security benefits of push architectures with the operational efficiency of modern programmable infrastructure. Banks and enterprises that understand this distinction and implement accordingly will find themselves better positioned to thrive in an increasingly complex threat landscape.
For businesses seeking to implement these advanced security architectures, the path forward involves partnering with platforms that specialize in programmable money APIs and DeFi infrastructure for banks. The technology exists today to implement secure, yield-generating payment systems that protect against fraud while creating new revenue opportunities.
Ready to Transform Your Payment Security Architecture?
The convergence of blockchain technology, programmable payments, and enterprise security creates unprecedented opportunities for forward-thinking financial institutions. Whether you're exploring crypto treasury management, implementing stablecoin business accounts, or developing comprehensive DeFi business banking solutions, the architectural decisions you make today will determine your competitive advantage tomorrow.
Discover how programmable payment architectures can revolutionize your enterprise security while generating yield on every transaction. The future of secure, profitable payments is available now.